BQT Biometrics Australia: Leading the Way in Biometric Security Technology
BQT Biometrics Australia: Leading the Way in Biometric Security Technology
Blog Article
Maximizing Service Protection: The Ultimate Guide to Electronic Security Solutions
In the hectic and ever-evolving landscape of service protection, the dependence on digital safety options has become critical for securing beneficial properties, confidential details, and maintaining operational connection. In this guide to electronic security remedies, we will certainly explore the newest fads, sophisticated modern technologies, and ideal methods to fortify your organization versus prospective risks and susceptabilities.
Significance of Electronic Safety Solutions
When taking into consideration the protection of properties and sensitive information, the significance of electronic security options can not be overstated. In today's interconnected world, where cyber hazards are continuously evolving and becoming a lot more sophisticated, services have to prioritize carrying out robust electronic protection measures to secure their information and procedures. Digital security services include a variety of innovations and techniques developed to protect against unapproved accessibility, data breaches, malware, and other cyber hazards.
One of the crucial advantages of digital security services is their capacity to give real-time surveillance and threat detection. BQT Locks. With devices like intrusion detection systems, firewalls, and security information and event management (SIEM) systems, companies can proactively recognize and react to safety occurrences prior to they intensify into significant violations. Furthermore, electronic safety and security options assist make certain compliance with sector laws and criteria, shielding services from prospective legal and economic effects
Kinds Of Electronic Safety And Security Systems
Provided the essential relevance of electronic safety remedies in safeguarding companies versus cyber hazards, it is crucial to check out the various sorts of digital protection systems readily available to improve protection and strength. One of one of the most usual kinds of electronic protection systems is the firewall software, which works as a barrier in between a firm's internal network and outside networks, straining potentially unsafe data. Breach Discovery Solution (IDS) are also vital, as they keep track of network website traffic for suspicious activity and sharp managers to potential dangers. Additionally, companies usually depend on encryption innovations to protect delicate data both at rest and in transportation. Access control systems, consisting of biometric visitors and keycard access, assistance manage access to physical spaces and secure properties. Video clip surveillance systems contribute in tracking and recording tasks within and around the facilities. By using a mix of these digital safety and security systems, organizations can develop a durable protection versus various security risks.
Applying Gain Access To Control Steps
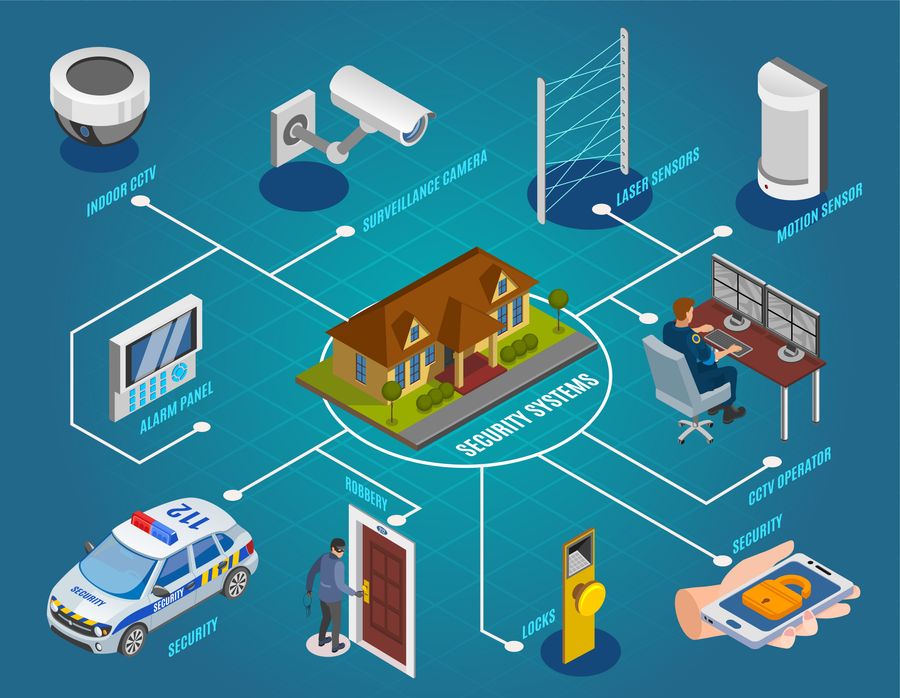
In addition, accessibility control steps can be incorporated with security systems to monitor and tape-record people' activities within safeguarded areas. This assimilation boosts security by offering a thorough overview of who is accessing particular places at any type of offered time. In addition, access control systems can be configured to restrict accessibility based on time, place, or individual credentials, allowing companies to personalize safety methods according to their specific demands.
Cybersecurity Finest Practices
To boost general safety pose, executing robust cybersecurity best methods is necessary in guarding digital assets and data honesty. One essential method is making certain routine software application updates across all tools and systems to spot vulnerabilities quickly. Employing strong, one-of-a-kind passwords and applying multi-factor authentication adds layers of protection against unapproved access. Conducting regular safety audits and assessments aids determine weaknesses and areas for improvement. Staff member training on cybersecurity understanding is crucial in protecting against social design attacks and making certain the original source a security-conscious labor force.
Developing a detailed incident action strategy enables swift and efficient responses to safety and security violations, minimizing prospective damage. Encrypting delicate information both en route and at rest supplies an additional barrier against information violations. Executing gain access to controls based upon the principle of least advantage restricts the exposure of vital systems and details to just those who require it for their duties. Regular backups of data make sure that in case of a ransomware attack or information loss, vital info can be recouped. Welcoming an aggressive approach to cybersecurity through continuous surveillance and risk intelligence helps discover and alleviate prospective dangers prior to they rise. By incorporating these finest methods into cybersecurity methods, services can strengthen their defenses against advancing cyber hazards.
Security and Surveillance Solutions

Video security services supply remote monitoring abilities, permitting authorized workers to keep an eye on the facilities also when off-site. In addition, advanced functions like activity detection, face recognition, and certificate plate acknowledgment enhance the general protection posture of the organization. Integrating monitoring systems with alarm systems and gain Find Out More access to control additionally strengthens the safety and security facilities, making it possible for a proactive reaction to possible protection violations.
Conclusion
In conclusion, digital protection options are vital for optimizing service defense. It is crucial to invest in the appropriate digital safety systems to guarantee the safety and security and safety of the organization.
Report this page